Really you all want your desktop clean from unwanted ICONS.
You can do that using below mentioned path:
START - RUN - GPEDIT.MSC - ADMINISTRATIVE TEMPLATES - SELECT DESKTOP -
In right pane select REMOVE COMPUTER ICON ON THE DESKTOP - RIGHT CLICK -
ENABLE - APPLY - OK.
CLOSE THE WINDOWS
You see your DESKTOP IS CLEAN FROM UNWANTED ICONS.
PROHIBITED ACCESS TO THE CONTROL PANEL
START - RUN - GPEDIT.MSC and hit ENTER
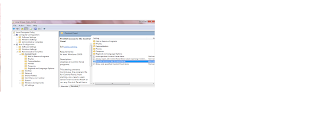
EXPAND ADMINISTRATIVE TOOLS - SELECT CONTROL PANEL - SEE RIGHT PANE -
- RIGHT CLICK ON Prohibit access to the Control Panel - EDIT - SELECT ENABLE
- OK AND CLOSE THE WINDOWS
As such you can prohibit more control panel functions.
* Ad or Remove Program
* Display
* Personalization
* Printer &
* Program etc.

EXPAND ADMINISTRATIVE TOOLS - SELECT CONTROL PANEL - SEE RIGHT PANE -
- RIGHT CLICK ON Prohibit access to the Control Panel - EDIT - SELECT ENABLE
- OK AND CLOSE THE WINDOWS
As such you can prohibit more control panel functions.
* Ad or Remove Program
* Display
* Personalization
* Printer &
* Program etc.
To invite a friend to help through remote assistance.
To invite a friend to help through remote assistance.
1. Go to the start menu. Choose Help and Support.
2. The Windows Help and Support dialog box will appear. Click on the link that says Use Windows Remote Assistance to get help from a friend or offer help.
3. Now to invite someone to help you, click on the Invite someone you trust to help you.
4. If you were Offering help to someone click on the button below.
5. The Windows Remote Assistance windows will appear. Press on use email to send an invitation.
6. You will need to enter a password. Remember this as you will need to give it to the person helping you.
7. Press next.
8. If you have Windows mail, Outlook, or even Thunderbird email it will open with the pre-filled details.
9. Enter the email address of who you want to send this invitation to.
10. Then type in the password you created.
11. Send the invitation to the Email recipient.
To take up this invitation the person who receives the email will need to save the attachment that came with it to their computer. Then they will need to follow the steps above, however they must choose to offer help to someone instead of asking for help
1. Go to the start menu. Choose Help and Support.
2. The Windows Help and Support dialog box will appear. Click on the link that says Use Windows Remote Assistance to get help from a friend or offer help.
3. Now to invite someone to help you, click on the Invite someone you trust to help you.
4. If you were Offering help to someone click on the button below.
5. The Windows Remote Assistance windows will appear. Press on use email to send an invitation.
6. You will need to enter a password. Remember this as you will need to give it to the person helping you.
7. Press next.
8. If you have Windows mail, Outlook, or even Thunderbird email it will open with the pre-filled details.
9. Enter the email address of who you want to send this invitation to.
10. Then type in the password you created.
11. Send the invitation to the Email recipient.
To take up this invitation the person who receives the email will need to save the attachment that came with it to their computer. Then they will need to follow the steps above, however they must choose to offer help to someone instead of asking for help
Add Items to the Start Button using Registry
Add Items to the Start Button using Registry
The best technique to edit the windows registry keys, always export or backup the whole windows registry keys on backup drive before editing. Because any mistake in Registry can cause serious problem in your computer to run properly.
Follow the given steps to change the Start button setting.
•First click on Start button then type Regedit in Run option.
•In Registry Editor go to left hand panel, and find HKey_Classes_Root / Directory / Shell
•Here Right click on Shell folder option and add any new key with descriptive name and Press Enter.
•Now Right click on that key and give the full path of that program you are interested to add in start button. For example if you want to add MS excel, then full path may be C:\program file\msoffice\msexcel.EXE.
•Now close all open programs and check the changes in your computer Start button.
The best technique to edit the windows registry keys, always export or backup the whole windows registry keys on backup drive before editing. Because any mistake in Registry can cause serious problem in your computer to run properly.
Follow the given steps to change the Start button setting.
•First click on Start button then type Regedit in Run option.
•In Registry Editor go to left hand panel, and find HKey_Classes_Root / Directory / Shell
•Here Right click on Shell folder option and add any new key with descriptive name and Press Enter.
•Now Right click on that key and give the full path of that program you are interested to add in start button. For example if you want to add MS excel, then full path may be C:\program file\msoffice\msexcel.EXE.
•Now close all open programs and check the changes in your computer Start button.
Allow users to Run only specified programs in Windows 7
Allow users to Run only specified programs in Windows 7
You can allow users to run only specified programs in Windows 7 operating systems. It is up to you if you want your shared computer to allow users to run only specified programs in Windows 7. A shared computer in an office, for example, can be set in the same way if the company does not want the employees to run all types of programs. You can allow the users to run only specified programs in Windows 7 by using the Local Group Policy. However, you cannot do this in the Home editions of Windows 7 as it does not provide the Local Group Policy Editor.
Click on the Start button.
Type “gpedit.msc” in the search box of the Start menu and press the Enter button on the keyboard.
Local Group Policy Editor will open. Scroll down to “User Configuration”, “Administrative Templates” and then “System” on the left hand side of the window pane.
On the right hand side of the window, under “Setting”, navigate and double-click on “Run only specified Windows applications”.
Select Enabled from the window.
Click on “Show” under Options.
The Show Contents window pane will appear. Here you can type the applications you want to let the users run.
After you are done, click on the OK button.
Close the Local Group Policy Editor.
After this, if someone attempts to run an app which was not specified by you, he will get this error message:
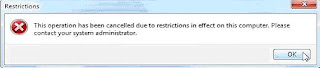
This feature to allow users to run only specified programs in Windows 7 is the best at preventing the users from accessing applications you don’t want them to use on a particular computer.
You can allow users to run only specified programs in Windows 7 operating systems. It is up to you if you want your shared computer to allow users to run only specified programs in Windows 7. A shared computer in an office, for example, can be set in the same way if the company does not want the employees to run all types of programs. You can allow the users to run only specified programs in Windows 7 by using the Local Group Policy. However, you cannot do this in the Home editions of Windows 7 as it does not provide the Local Group Policy Editor.
Click on the Start button.
Type “gpedit.msc” in the search box of the Start menu and press the Enter button on the keyboard.
Local Group Policy Editor will open. Scroll down to “User Configuration”, “Administrative Templates” and then “System” on the left hand side of the window pane.
On the right hand side of the window, under “Setting”, navigate and double-click on “Run only specified Windows applications”.
Select Enabled from the window.
Click on “Show” under Options.
The Show Contents window pane will appear. Here you can type the applications you want to let the users run.
After you are done, click on the OK button.
Close the Local Group Policy Editor.
After this, if someone attempts to run an app which was not specified by you, he will get this error message:

This feature to allow users to run only specified programs in Windows 7 is the best at preventing the users from accessing applications you don’t want them to use on a particular computer.
SHORT CUT FOR LOCKING THE COMPUTER SCREEN IN WINDOWS 7
SHORT CUT FOR LOCKING THE COMPUTER SCREEN IN WINDOWS 7
There are many ways in which you can lock the computer screen. The most popular as well as the fastest way to lock it is to use a keyboard shortcut. The keyboard shortcut used to lock the computer screen is Win+L. A few of us choose to utilize the mouse to lock it. And of course many people like to use both the options.
There is another method in which we can lock the computer screen. It is to create a shortcut for locking the computer screen in Windows 7. You can create a shortcut for locking the computer screen in Windows 7, XP and Vista too. Follow these steps in order to create a shortcut for locking the computer screen in Windows 7 as well as other editions:
Right-click on the desktop where you would like to create the shortcut.
Point to New.
Click on Shortcut from the menu.
Type in this text in the shortcut textbox. (This text will work for Windows XP as well even though the screen will be different)
rundll32.exe user32.dll, LockWorkStation
Click on the Next button.
Type in a name for your shortcut.
Click on the Finish button.
You have successfully created a shortcut to lock your workstation. Just click on the shortcut whenever you want to lock the computer screen.
There are many ways in which you can lock the computer screen. The most popular as well as the fastest way to lock it is to use a keyboard shortcut. The keyboard shortcut used to lock the computer screen is Win+L. A few of us choose to utilize the mouse to lock it. And of course many people like to use both the options.
There is another method in which we can lock the computer screen. It is to create a shortcut for locking the computer screen in Windows 7. You can create a shortcut for locking the computer screen in Windows 7, XP and Vista too. Follow these steps in order to create a shortcut for locking the computer screen in Windows 7 as well as other editions:
Right-click on the desktop where you would like to create the shortcut.
Point to New.
Click on Shortcut from the menu.
Type in this text in the shortcut textbox. (This text will work for Windows XP as well even though the screen will be different)
rundll32.exe user32.dll, LockWorkStation
Click on the Next button.
Type in a name for your shortcut.
Click on the Finish button.
You have successfully created a shortcut to lock your workstation. Just click on the shortcut whenever you want to lock the computer screen.
Disable search history display in Windows 7
Windows 7 automatically saves all the recent searches done by the users. Some people are annoyed by this feature as the last three searches become visible under the search box as you start typing in it. If the computer is shared by others, you might not want others to see your past searches. There is a way in which you can disable search history display in Windows 7. However, you cannot disable search history display in Windows 7 Home editions. This is due to the fact that you need to utilize the Group Policy Editor for achieving this goal and it is not available in the Home versions. Follow these steps to disable search history display in Windows 7:
Enter gpedit.msc in the search box of the Start menu. Press Enter. This will open the Local Group Policy Editor.
Scroll down to User Configuration \ Administrative Templates \ Windows Components \ Windows Explorer.
Double-click on Turn off display of recent search entries in the Windows Explorer search box on the right hand side of the dialog box.
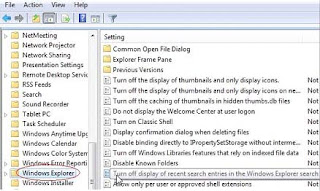
Select Enabled and click on the Apply button.
Click on the OK button.
Close out of the Group Policy Editor.
From now on, you won't be bothered by the display of recent search history as you start typing into the search box.
Enter gpedit.msc in the search box of the Start menu. Press Enter. This will open the Local Group Policy Editor.
Scroll down to User Configuration \ Administrative Templates \ Windows Components \ Windows Explorer.
Double-click on Turn off display of recent search entries in the Windows Explorer search box on the right hand side of the dialog box.

Select Enabled and click on the Apply button.
Click on the OK button.
Close out of the Group Policy Editor.
From now on, you won't be bothered by the display of recent search history as you start typing into the search box.
Removing autorun.inf from USB pendisks and Hard Drive
Most of the people are facing computer due to autorun.inf that are placed inside pendisks that manage quickly infect computers when users double-click on the icon to open the pendisk.
A virulent computer will add these files on the root of a target USB disk:
CODE
autorun.inf
Recycled [folder]
Recycled\ctfmon.exe
If you think your computer is safe - open up windows explorer --> Tools --> Folder Options --> Check "Show Hidden system files"
And take another look.
---
Now, I'll mention a way to remove these annoying files but it would be nice to know which other techniques exist out there to remove this menace.
Let's imagine that on this example your USB disk is placed on drive E:
- You open up a command prompt window (type cmd.exe on the run window)
- Let's remove the pesky file - type:
CODE
erase E:\aurorun.inf /f /a
- Add a dummy folder:
CODE
md E:\autorun.inf
- Add write protection:
CODE
attrib +s +h +r E:\autorun.inf
This is what I use to make my pendisks immune to virus whenever walking around several other machines.
A virulent computer will try to create a autorun.inf on the root of the pendisk but as a folder already exists this operation won't be possible. Some virus might try to delete this folder, but since we add the additional protection attributes - it will be somewhat safer.
A virulent computer will add these files on the root of a target USB disk:
CODE
autorun.inf
Recycled [folder]
Recycled\ctfmon.exe
If you think your computer is safe - open up windows explorer --> Tools --> Folder Options --> Check "Show Hidden system files"
And take another look.
---
Now, I'll mention a way to remove these annoying files but it would be nice to know which other techniques exist out there to remove this menace.
Let's imagine that on this example your USB disk is placed on drive E:
- You open up a command prompt window (type cmd.exe on the run window)
- Let's remove the pesky file - type:
CODE
erase E:\aurorun.inf /f /a
- Add a dummy folder:
CODE
md E:\autorun.inf
- Add write protection:
CODE
attrib +s +h +r E:\autorun.inf
This is what I use to make my pendisks immune to virus whenever walking around several other machines.
A virulent computer will try to create a autorun.inf on the root of the pendisk but as a folder already exists this operation won't be possible. Some virus might try to delete this folder, but since we add the additional protection attributes - it will be somewhat safer.
Enable the Acrobat reader embed video icon in MS Word 2007
Enable the Acrobat reader embed video icon in MS Word 2007
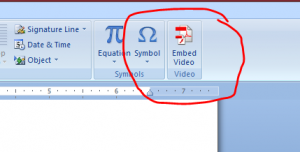
Are you missing the Acrobat Reader Embed Video icon in Word 2007 insert menu? Previously I wrote a tutorial on how to embed video into Word 2007 and convert it to PDF. So many people responded on the website and on Youtube asking where their embed video icon was? “I have a full version of Adobe Acrobat and Word 2007, why can’t I see the embed video icon?” That’s what they were saying…Well I really had no idea because I had one and didn’t have a problem. Anyway it annoyed me that so many people had this problem so I search for an answer, which in the end, turned out to be an easy solution.
add video icon Word 2007
What you need to have a Embed Video icon in Word 2007?
1. You need Microsoft Word 2007 installed on your computer.
2. You also need a full version of Adobe acrobat reader. Not the free version.
How to enable the Acrobat Reader add video icon in Word 2007?
1. Open Word 2007 and go to the round office icon in the left top corner.
2. Open the menu and go to the bottom and choose Word Options. See the screen shot below.
word options 2007
3. Click on Add ins in the left bar.
4. Now you can see if your Adobe Acrobat reader is an active application or a disabled application.
5. If your Adobe is under the disabled application section move down to the manage section at the bottom of the window.
6. From the drop down menu choose disabled items.
Adobe acrobat add in
7. A small box will appear. Choose the application you want to enable by making it blue.
8. Then press the enable button.
9. Restart the program to see that the Adobe Acrobat add video icon is there now..
Watch this video tutorial to see how to get your Adobe Acrobat Embed video icon back in Word 2007:
Are you missing the Acrobat Reader Embed Video icon in Word 2007 insert menu? Previously I wrote a tutorial on how to embed video into Word 2007 and convert it to PDF. So many people responded on the website and on Youtube asking where their embed video icon was? “I have a full version of Adobe Acrobat and Word 2007, why can’t I see the embed video icon?” That’s what they were saying…Well I really had no idea because I had one and didn’t have a problem. Anyway it annoyed me that so many people had this problem so I search for an answer, which in the end, turned out to be an easy solution.
add video icon Word 2007
What you need to have a Embed Video icon in Word 2007?
1. You need Microsoft Word 2007 installed on your computer.
2. You also need a full version of Adobe acrobat reader. Not the free version.
How to enable the Acrobat Reader add video icon in Word 2007?
1. Open Word 2007 and go to the round office icon in the left top corner.
2. Open the menu and go to the bottom and choose Word Options. See the screen shot below.
word options 2007
3. Click on Add ins in the left bar.
4. Now you can see if your Adobe Acrobat reader is an active application or a disabled application.
5. If your Adobe is under the disabled application section move down to the manage section at the bottom of the window.
6. From the drop down menu choose disabled items.
Adobe acrobat add in
7. A small box will appear. Choose the application you want to enable by making it blue.
8. Then press the enable button.
9. Restart the program to see that the Adobe Acrobat add video icon is there now..
Watch this video tutorial to see how to get your Adobe Acrobat Embed video icon back in Word 2007:
YOUR CHILD HAVE A FACEBOOK PAGE
Here are steps you should take if you do let your child have a Facebook page:
1. The first thing you can do is get your kid’s user name and password so that you can log onto their profile at any time and see what messages and conversations they’ve been sending. If they are not happy with this, then don’t let them have an account.
2. Another tactic to approach when deciding what age is too young for Facebook is to install surveillance software on your computer. Much like a Fortune 500 company tracks every trade proposal their salespeople are sending in Fantasy Football, you can monitor every single keystroke with some relatively inexpensive software.
3. Do not let your child be friends with people out of their age group. For example my 13 year old daughter is friends with my 18 year old next door neighbour, nice boy and all, but is talking about things I would prefer my daughter not to see.
4. The child must personally know the people they are friends with. Not a friend they met online. We all know how easy it is to make a fake profile, and just be aware that anyone can do it!
5. If you’ve tried but eventually decided your little one is too young for Facebook, just block the site on your computer with an administrative password so that you’ll still be able to log on. Here’s how to Setup parental controls in Windows Seven and Vista.
6. And finally, the last step you can take to keep your kid off Facebook is to spend some time with them – even with all the latest advances in technology nothing will ever top a good game of catch or monopoly.
Too young for Facebook
1. The first thing you can do is get your kid’s user name and password so that you can log onto their profile at any time and see what messages and conversations they’ve been sending. If they are not happy with this, then don’t let them have an account.
2. Another tactic to approach when deciding what age is too young for Facebook is to install surveillance software on your computer. Much like a Fortune 500 company tracks every trade proposal their salespeople are sending in Fantasy Football, you can monitor every single keystroke with some relatively inexpensive software.
3. Do not let your child be friends with people out of their age group. For example my 13 year old daughter is friends with my 18 year old next door neighbour, nice boy and all, but is talking about things I would prefer my daughter not to see.
4. The child must personally know the people they are friends with. Not a friend they met online. We all know how easy it is to make a fake profile, and just be aware that anyone can do it!
5. If you’ve tried but eventually decided your little one is too young for Facebook, just block the site on your computer with an administrative password so that you’ll still be able to log on. Here’s how to Setup parental controls in Windows Seven and Vista.
6. And finally, the last step you can take to keep your kid off Facebook is to spend some time with them – even with all the latest advances in technology nothing will ever top a good game of catch or monopoly.
Too young for Facebook
COMPUTER SECURITY TIPS
Top Ten Computer Security Tips
Computer security is an essential part of getting (and keeping) your computer connected to the Iowa State network. With new security risks appearing every day, keeping your computer secure is a continuing process. Even new computers are not secure until they have anti-virus software in use, current security patches, and strong passwords. Following is a set of tips to help keep your computer secure and functioning properly.
Tip 1: Use anti-virus software and keep it up-to-date.
Anti-virus software protects you and your computer from viruses, a well-known security risk. With new viruses appearing daily, virus software quickly becomes useless if you don't update it.
Tip 2: Use an anti-spyware program.
Free tools are available for identifying and removing spyware, adware, and various other non-virus malware. These types of files are often installed by Trojan programs, some freeware and shareware applications programs (like file-sharing programs), or as "drive-by installations" from various websites. These programs invade your privacy and interfere with your work by transmitting your personal information to their creators, opening unwanted pop-up windows, and noticeably slowing your computer's performance.
Iowa State students can download the McAfee Anti-Spyware Enterprise software for Windows at no cost from http://www.it.iastate.edu/downloads/. (Use the Scout utility to install the software.) The university has licensed this package so students have convenient spyware protection and removal for their computers. The package works in conjunction with the McAfee anti-virus software, or can be installed as a standalone product with other anti-virus software.
Information on other free anti-spyware programs for Windows machines can be found at http://www.it.iastate.edu/faq/view.php?id=179. Currently, spyware is not a problem for Macintosh computers.
Tip 3: Keep your operating system and other software current.
Keep your operating system up-to-date as well as any programs used to access the Internet. When manufacturers find vulnerabilities that pose security risks, they create and distribute patches for the product. To make sure that your system is patched with the latest updates, check the information at:
* Windows XP: http://www.it.iastate.edu/faq/view.php?id=150
* Windows 2000: http://www.it.iastate.edu/faq/view.php?id=261
* Mac OS X: http://www.it.iastate.edu/faq/view.php?id=532
Tip 4. Do not download files from an unknown source.
Be careful of what you download and what you agree to when you click "yes" to prompts from installation or popup windows. Many programs do more than what they advertise. Many "web browser aids", such as gator.com and Bonzi Buddy, are actually spyware (i.e., programs that send information about your browsing habits back to their home server and cause popup windows). After collecting information on your browsing habits, the spyer then sells the information to companies that send you unwanted email. Also, be wary of downloaded programs that seem to do good things because they could actually be causing harm or opening up new security holes on your computer. A number of programs are designed to give other people access to your computer without your knowledge. Often anti-virus or anti-spyware software will be able to detect such programs; caution, however, is the best protection.
Tip 5: Use complex, hard-to-guess passwords and change them regularly.
Any security measures you take can be undermined by a password that is easy to guess or a computer account that does not have a password. Good passwords help keep your computer secure from external threats (such as hackers) and local threats (such as a nosy roommate or officemate).
* Never have an account without a password.
* We recommend using 15 or more characters whenever possible for your password (5 characters is a minimum).
* Use a mixture of character classes such as uppercase, lowercase, numbers, and symbols.
* Don't use a password that is a dictionary word, is part of your name, or is easily associated with you.
* Never use keyboard patterns such as "asdfg".
* Passphrases are a good technique for remembering a long password so you don't have to write it down (e.g., "Ihatestalebread!").
* Use different passwords for your important computer accounts. Although somewhat inconvenient, if one of your passwords is compromised, an attacker will not gain easy access to your other accounts.
* If you use your password in public places, such as a lab or a friend's room, you should change your password more often.
Before connecting your computer to the network, make sure you have a password set on all of your login accounts, including your administrative (a.k.a. admin) account. For instructions, follow the appropriate link:
* Windows XP: http://www.it.iastate.edu/faq/view.php?id=99
* Macintosh OS X: http://www.it.iastate.edu/faq/view.php?id=98
Tip 6. Do not open emails or attachments from unknown sources.
Email is one of the easiest ways to transmit computer viruses and Trojan programs, which can give other people access to your computer. If you don't recognize the email sender, don't open the attachment(s) with it. If you get an attachment from someone you know but weren't expecting one, don't open it until you ask the sender about it.
Tip 7. Use file sharing sparingly.
Windows computers that have Microsoft File Sharing enabled are frequently probed by hackers and viruses for weakness. We recommend that you share folders sparingly. When needed, turn on sharing for a specific purpose, specify a password, and remove sharing when it is not needed. Warning: By default, shared folders are set so anyone can read and write into the folder. Also, the installation of peer-to-peer file sharing programs can bring spyware onto your computer and open it up to some viruses. Most file sharing programs also default to opening shared folders for read and write access, allowing distribution of the folder contents.
Tip 8. Only run services that you need.
Each network service that is installed on your computer opens a network port that can be probed by hackers and viruses. Resist the temptation to experiment with network services that you are not likely to use. Commonly targeted services are IIS (Microsoft's Web server), ftp (file transfer protocol), telnet (remote login to a command prompt), Upnp (universal plug and play) and Microsoft File Sharing.
Tip 9: Use a firewall to protect your computer from Internet intruders.
Computers connected to the Internet should use a personal firewall to filter out unauthorized or potentially dangerous traffic from the Internet, while allowing good traffic to reach your computer. Firewall hardware and software is available at computer stores and is built in to some operating systems/updates, such as Windows XP Service Pack 2 (SP2). We recommend that you block all ports that you do not use. Note that some Iowa State software will not run from behind a firewall.
Tip 10. Back up your computer data regularly.
The failure of a computer hard drive or the mistaken deletion of a data file can be devastating to the individual and can mean the loss of many hours of work. Recovery from hardware or software malfunctions and user errors can be easier if regular backups are made. To guard against disasters, store backups in a separate location from your computer.
Computer security is an essential part of getting (and keeping) your computer connected to the Iowa State network. With new security risks appearing every day, keeping your computer secure is a continuing process. Even new computers are not secure until they have anti-virus software in use, current security patches, and strong passwords. Following is a set of tips to help keep your computer secure and functioning properly.
Tip 1: Use anti-virus software and keep it up-to-date.
Anti-virus software protects you and your computer from viruses, a well-known security risk. With new viruses appearing daily, virus software quickly becomes useless if you don't update it.
Tip 2: Use an anti-spyware program.
Free tools are available for identifying and removing spyware, adware, and various other non-virus malware. These types of files are often installed by Trojan programs, some freeware and shareware applications programs (like file-sharing programs), or as "drive-by installations" from various websites. These programs invade your privacy and interfere with your work by transmitting your personal information to their creators, opening unwanted pop-up windows, and noticeably slowing your computer's performance.
Iowa State students can download the McAfee Anti-Spyware Enterprise software for Windows at no cost from http://www.it.iastate.edu/downloads/. (Use the Scout utility to install the software.) The university has licensed this package so students have convenient spyware protection and removal for their computers. The package works in conjunction with the McAfee anti-virus software, or can be installed as a standalone product with other anti-virus software.
Information on other free anti-spyware programs for Windows machines can be found at http://www.it.iastate.edu/faq/view.php?id=179. Currently, spyware is not a problem for Macintosh computers.
Tip 3: Keep your operating system and other software current.
Keep your operating system up-to-date as well as any programs used to access the Internet. When manufacturers find vulnerabilities that pose security risks, they create and distribute patches for the product. To make sure that your system is patched with the latest updates, check the information at:
* Windows XP: http://www.it.iastate.edu/faq/view.php?id=150
* Windows 2000: http://www.it.iastate.edu/faq/view.php?id=261
* Mac OS X: http://www.it.iastate.edu/faq/view.php?id=532
Tip 4. Do not download files from an unknown source.
Be careful of what you download and what you agree to when you click "yes" to prompts from installation or popup windows. Many programs do more than what they advertise. Many "web browser aids", such as gator.com and Bonzi Buddy, are actually spyware (i.e., programs that send information about your browsing habits back to their home server and cause popup windows). After collecting information on your browsing habits, the spyer then sells the information to companies that send you unwanted email. Also, be wary of downloaded programs that seem to do good things because they could actually be causing harm or opening up new security holes on your computer. A number of programs are designed to give other people access to your computer without your knowledge. Often anti-virus or anti-spyware software will be able to detect such programs; caution, however, is the best protection.
Tip 5: Use complex, hard-to-guess passwords and change them regularly.
Any security measures you take can be undermined by a password that is easy to guess or a computer account that does not have a password. Good passwords help keep your computer secure from external threats (such as hackers) and local threats (such as a nosy roommate or officemate).
* Never have an account without a password.
* We recommend using 15 or more characters whenever possible for your password (5 characters is a minimum).
* Use a mixture of character classes such as uppercase, lowercase, numbers, and symbols.
* Don't use a password that is a dictionary word, is part of your name, or is easily associated with you.
* Never use keyboard patterns such as "asdfg".
* Passphrases are a good technique for remembering a long password so you don't have to write it down (e.g., "Ihatestalebread!").
* Use different passwords for your important computer accounts. Although somewhat inconvenient, if one of your passwords is compromised, an attacker will not gain easy access to your other accounts.
* If you use your password in public places, such as a lab or a friend's room, you should change your password more often.
Before connecting your computer to the network, make sure you have a password set on all of your login accounts, including your administrative (a.k.a. admin) account. For instructions, follow the appropriate link:
* Windows XP: http://www.it.iastate.edu/faq/view.php?id=99
* Macintosh OS X: http://www.it.iastate.edu/faq/view.php?id=98
Tip 6. Do not open emails or attachments from unknown sources.
Email is one of the easiest ways to transmit computer viruses and Trojan programs, which can give other people access to your computer. If you don't recognize the email sender, don't open the attachment(s) with it. If you get an attachment from someone you know but weren't expecting one, don't open it until you ask the sender about it.
Tip 7. Use file sharing sparingly.
Windows computers that have Microsoft File Sharing enabled are frequently probed by hackers and viruses for weakness. We recommend that you share folders sparingly. When needed, turn on sharing for a specific purpose, specify a password, and remove sharing when it is not needed. Warning: By default, shared folders are set so anyone can read and write into the folder. Also, the installation of peer-to-peer file sharing programs can bring spyware onto your computer and open it up to some viruses. Most file sharing programs also default to opening shared folders for read and write access, allowing distribution of the folder contents.
Tip 8. Only run services that you need.
Each network service that is installed on your computer opens a network port that can be probed by hackers and viruses. Resist the temptation to experiment with network services that you are not likely to use. Commonly targeted services are IIS (Microsoft's Web server), ftp (file transfer protocol), telnet (remote login to a command prompt), Upnp (universal plug and play) and Microsoft File Sharing.
Tip 9: Use a firewall to protect your computer from Internet intruders.
Computers connected to the Internet should use a personal firewall to filter out unauthorized or potentially dangerous traffic from the Internet, while allowing good traffic to reach your computer. Firewall hardware and software is available at computer stores and is built in to some operating systems/updates, such as Windows XP Service Pack 2 (SP2). We recommend that you block all ports that you do not use. Note that some Iowa State software will not run from behind a firewall.
Tip 10. Back up your computer data regularly.
The failure of a computer hard drive or the mistaken deletion of a data file can be devastating to the individual and can mean the loss of many hours of work. Recovery from hardware or software malfunctions and user errors can be easier if regular backups are made. To guard against disasters, store backups in a separate location from your computer.
COMPUTER VIRUS
A small program that gets into your computer and disturbs the normal functions of the computer and destroys the important data stored in the computer is called computer virus. The computer virus cannot damage hardware, only data or software is corrupted. The computer file (data or program) to which a virus is attached is called infected file.
A program, which is infected by a virus, is known as infected program. When an infected program is loaded for execution, the virus automatically loaded into memory and attaches to all those programs that are in memory or loaded into memory.
Causes of Viruses
Following are the means through which viruses may be transferred from one computer to another.
(i) E-Mail
Now-a-days, most of the viruses spread due to receiving e-mail messages that contains viruses. When a user opens such an infected message, the virus is also loaded into the computer memory and attaches copies of it-self with many other program files loaded into the memory. This virus is also transferred to other computers when e-mail messages are sent from the infected computer to them.
(ii) Networks
Another way of spreading virus is by using Internet and other networks. For example, when you download some executable file or data on the Internet or from a shared disk on the Network, the infected files may be attached with the downloaded data that ultimately infects the computer.
(iii) Removable Storage Media
One important means of exchanging data is through the use of removable media like floppy disks, CDs and flash devices. So, when you copy the data from one computer to another by using a removable media, the infected files can be transferred to your computer.
(iv) Pirated Software
The virus can also infect your computer by using pirated software. The software, which is installed into your computer without license is referred to as pirated software. Some companies may intentionally attach some virus programs into their software. This program will only activate when it does not find some special file like license file on your computer.
A program, which is infected by a virus, is known as infected program. When an infected program is loaded for execution, the virus automatically loaded into memory and attaches to all those programs that are in memory or loaded into memory.
Causes of Viruses
Following are the means through which viruses may be transferred from one computer to another.
(i) E-Mail
Now-a-days, most of the viruses spread due to receiving e-mail messages that contains viruses. When a user opens such an infected message, the virus is also loaded into the computer memory and attaches copies of it-self with many other program files loaded into the memory. This virus is also transferred to other computers when e-mail messages are sent from the infected computer to them.
(ii) Networks
Another way of spreading virus is by using Internet and other networks. For example, when you download some executable file or data on the Internet or from a shared disk on the Network, the infected files may be attached with the downloaded data that ultimately infects the computer.
(iii) Removable Storage Media
One important means of exchanging data is through the use of removable media like floppy disks, CDs and flash devices. So, when you copy the data from one computer to another by using a removable media, the infected files can be transferred to your computer.
(iv) Pirated Software
The virus can also infect your computer by using pirated software. The software, which is installed into your computer without license is referred to as pirated software. Some companies may intentionally attach some virus programs into their software. This program will only activate when it does not find some special file like license file on your computer.
STARTUP FOLDER FUN
Startup Folder Fun
While we’re on the topic of system startups, the Windows Startup folder is a fantastic place for fun. Create a text file with an amusing message and throw it in there so your cubicle mate will get a daily greeting — or, if you really want to get evil, add in the restart shortcut from above (not recommended unless you just want to get your ass kicked).
While we’re on the topic of system startups, the Windows Startup folder is a fantastic place for fun. Create a text file with an amusing message and throw it in there so your cubicle mate will get a daily greeting — or, if you really want to get evil, add in the restart shortcut from above (not recommended unless you just want to get your ass kicked).
SCREEN CAPTURE OR PRINT SCREEN
Screen Capture or Print Screen
While many people are well familiar with "taking a screen-shot of your PC", some others might wonder what it is. On an Windows PC, the "Print Screen" feature can either capture the entire screen of your PC, or an individual window. This is a simple but very helpful tip. Once you know about it, you will find it very useful in many situations, i.e. when you need to show a tech-support person an error alert on your screen, or a sample screen of an application software...
The following instructions will show you how to capture a screen shot of your entire desktop or an individual window. On most standard keyboards, the print screen button is often identified as "Print Scrn".
To capture a screen shot of your entire desktop:
1. Hit "Print Screen" key on your keyboard (or "Print Scrn").
2. Open an image editor (i.e. Photoshop, Paintshop, or the Windows built-in "Paint").
3. Press Ctrl-V to paste the image and save the file as your favorite picture format (i.e. *.JPG).
To capture a screen shot of an individual window, a popup, or an error dialog:
1. Make sure the window or popup which you want to capture is active (on the very front of your screen).
2. Hold the "Alt" button and press "Print Screen" key on your keyboard (or "Print Scrn").
3. Open an image editor and press Ctrl-V to paste the image and save the file as your favorite picture format (i.e. *.JPG).
While many people are well familiar with "taking a screen-shot of your PC", some others might wonder what it is. On an Windows PC, the "Print Screen" feature can either capture the entire screen of your PC, or an individual window. This is a simple but very helpful tip. Once you know about it, you will find it very useful in many situations, i.e. when you need to show a tech-support person an error alert on your screen, or a sample screen of an application software...
The following instructions will show you how to capture a screen shot of your entire desktop or an individual window. On most standard keyboards, the print screen button is often identified as "Print Scrn".
To capture a screen shot of your entire desktop:
1. Hit "Print Screen" key on your keyboard (or "Print Scrn").
2. Open an image editor (i.e. Photoshop, Paintshop, or the Windows built-in "Paint").
3. Press Ctrl-V to paste the image and save the file as your favorite picture format (i.e. *.JPG).
To capture a screen shot of an individual window, a popup, or an error dialog:
1. Make sure the window or popup which you want to capture is active (on the very front of your screen).
2. Hold the "Alt" button and press "Print Screen" key on your keyboard (or "Print Scrn").
3. Open an image editor and press Ctrl-V to paste the image and save the file as your favorite picture format (i.e. *.JPG).
HOW TO OPEN OFFICE 2007 FILES INTO OFFICE 2003
How to open office 2007 files into Office 2003
Today tip will help you to resolve the compatibility issues between the Office 2003 and Office 2007. Because all programs in office 2003 used the old file extensions for its different programs. For example Word 2003 saved files with extension .doc, Excel 2003 with .xls and PowerPoint with .ppt. but on the other office 2007 used the new file extensions for its different programs. For example Word 2007 saved files with extension .docx, Excel 2007 with .xlsx and PowerPoint with .pptx. Now the problem is that when you will try to open office 2007 files into office 2003 and you will not open the file due to compatibility issues between both office versions. Microsoft provides a free compatibility pack to convert office 2007 documents to the office 2003 format. There are many third party free converter are available but here we are using Microsoft office compatibility pack.
Follow the given steps to download free Microsoft compatibility pack and install it.
To use this feature, you will need to be logged into your computer with administrative rights.
Visit the following link to download the Microsoft compatibility pack:
http://www.microsoft.com/downloads/details.aspx?FamilyId=941b3470-3ae9-4aee-8f43-c6bb74cd1466&displaylang=en
Today tip will help you to resolve the compatibility issues between the Office 2003 and Office 2007. Because all programs in office 2003 used the old file extensions for its different programs. For example Word 2003 saved files with extension .doc, Excel 2003 with .xls and PowerPoint with .ppt. but on the other office 2007 used the new file extensions for its different programs. For example Word 2007 saved files with extension .docx, Excel 2007 with .xlsx and PowerPoint with .pptx. Now the problem is that when you will try to open office 2007 files into office 2003 and you will not open the file due to compatibility issues between both office versions. Microsoft provides a free compatibility pack to convert office 2007 documents to the office 2003 format. There are many third party free converter are available but here we are using Microsoft office compatibility pack.
Follow the given steps to download free Microsoft compatibility pack and install it.
To use this feature, you will need to be logged into your computer with administrative rights.
Visit the following link to download the Microsoft compatibility pack:
http://www.microsoft.com/downloads/details.aspx?FamilyId=941b3470-3ae9-4aee-8f43-c6bb74cd1466&displaylang=en
COMMAND PROMPT ON RIGHT CLICK
Command Prompt on Right-Click
Many computer users, specially the programmers, need to launch a command prompt window every once in a while to execute some dos/shell commands. The problem is, when a command prompt window launched, the default path is normally the system path or the user profile's path. The users will then have to do all the "cd" commands to change the directories to the path he/she wants.
This trick shows you how to add an option called "Command Prompt" when you right-click on a folder in Windows. With this option, a Command Prompt Window will launch and its current directory will be the path to the folder you've selected.
Use this trick at your own risk.
Here's what you'll get:
The Solution
You can either edit your registry OR download the registry file and apply it on your computer.
Method I. Manually edit the registry:
1.Start > Run
2.Enter "regedit" and hit Enter
3.Expand to "HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shell"
4.Right-click on "shell" and select New > Key
5.Make sure a new key is created under "shell". Change the name of this key to "Command Prompt"
6.Right-click on this new key "Command Prompt" and select New > Key
7.Change the name of this key to "command"
8.Here's what we should have:
9.Double-click on the "(Default)" text on the right window to bring up the edit box
10.Enter this text into the Value Data field:
cmd.exe "%1"
11.Click OK and close the registry.
Many computer users, specially the programmers, need to launch a command prompt window every once in a while to execute some dos/shell commands. The problem is, when a command prompt window launched, the default path is normally the system path or the user profile's path. The users will then have to do all the "cd" commands to change the directories to the path he/she wants.
This trick shows you how to add an option called "Command Prompt" when you right-click on a folder in Windows. With this option, a Command Prompt Window will launch and its current directory will be the path to the folder you've selected.
Use this trick at your own risk.
Here's what you'll get:
The Solution
You can either edit your registry OR download the registry file and apply it on your computer.
Method I. Manually edit the registry:
1.Start > Run
2.Enter "regedit" and hit Enter
3.Expand to "HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shell"
4.Right-click on "shell" and select New > Key
5.Make sure a new key is created under "shell". Change the name of this key to "Command Prompt"
6.Right-click on this new key "Command Prompt" and select New > Key
7.Change the name of this key to "command"
8.Here's what we should have:
9.Double-click on the "(Default)" text on the right window to bring up the edit box
10.Enter this text into the Value Data field:
cmd.exe "%1"
11.Click OK and close the registry.
HOW TO OPERATE MOUSE POINTER WITHOUT MOUSE
How to Operate Mouse Pointer Without Mouse
This trick is a user contributed. The information might have been copied and pasted exactly as what user posted.
Proceed at your own risks.
You have Mouse Problem ?? No Problem
I will give you suggestion
Press Left Alt + Left Shift + Num Lock Button + Ok
with the help of Numeric Keypad e.g ( Press and Hold the following Keys )
7 8 9
4 6
1 2 3
For Normal Click Press 5
Default
Left Alt + Left Shift + Num Lock
This trick is a user contributed. The information might have been copied and pasted exactly as what user posted.
Proceed at your own risks.
You have Mouse Problem ?? No Problem
I will give you suggestion
Press Left Alt + Left Shift + Num Lock Button + Ok
with the help of Numeric Keypad e.g ( Press and Hold the following Keys )
7 8 9
4 6
1 2 3
For Normal Click Press 5
Default
Left Alt + Left Shift + Num Lock
HIDE ALL DRIVES FROM MY COMPUTER
Hide all drives from My Computer
This trick is a user contributed. The information might have been copied and pasted exactly as what user posted.
Proceed at your own risks.
How to Hide the drives(c:,d:,e:,...etc) in Ur Computer
This is a great trick you can play on your friends. To disable the display of local or networked drives when you click My Computer.
1.Go to Start -> Run.
2.Type regedit
3.Now go to: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
4.Now in the right pane, create a new DWORD item and name it NoDrives (it is case sensitive).
5.Now modify it's value and set it to 3FFFFFF (Hexadecimal) .
6.Now restart your computer.
7.So, now when you click on My Computer, no drives will be shown(all gone...).
To enable display of drives in My Computer, simply delete this DWORD item that you created. Again restart your computer. You can now see all the drives again.
This trick is a user contributed. The information might have been copied and pasted exactly as what user posted.
Proceed at your own risks.
How to Hide the drives(c:,d:,e:,...etc) in Ur Computer
This is a great trick you can play on your friends. To disable the display of local or networked drives when you click My Computer.
1.Go to Start -> Run.
2.Type regedit
3.Now go to: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
4.Now in the right pane, create a new DWORD item and name it NoDrives (it is case sensitive).
5.Now modify it's value and set it to 3FFFFFF (Hexadecimal) .
6.Now restart your computer.
7.So, now when you click on My Computer, no drives will be shown(all gone...).
To enable display of drives in My Computer, simply delete this DWORD item that you created. Again restart your computer. You can now see all the drives again.
WINDOWS 7 - THE BLACK BOX RECORDER
The Black Box Recorder
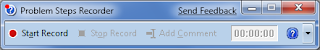
Every developer wishes there was a way that an end-users could quickly and simply record a repro for the problem that they’re running into that is unique to their machine. Windows 7 comes to the rescue! Part of the in-built diagnostic tools that we use internally to send feedback on the product, the Problem Steps Recorder provides a simple screen capture tool that enables you to record a series of actions. Once you hit “record”, it tracks your mouse and keyboard and captures screenshots with any comments you choose to associate alongside them. Once you stop recording, it saves the whole thing to a ZIP file, containing an HTML-based “slide show” of the steps. It’s a really neat little tool and I can’t wait for it to become ubiquitous on every desktop! The program is called psr.exe; you can also search for it from Control Panel under “Record steps to reproduce a problem”.

Every developer wishes there was a way that an end-users could quickly and simply record a repro for the problem that they’re running into that is unique to their machine. Windows 7 comes to the rescue! Part of the in-built diagnostic tools that we use internally to send feedback on the product, the Problem Steps Recorder provides a simple screen capture tool that enables you to record a series of actions. Once you hit “record”, it tracks your mouse and keyboard and captures screenshots with any comments you choose to associate alongside them. Once you stop recording, it saves the whole thing to a ZIP file, containing an HTML-based “slide show” of the steps. It’s a really neat little tool and I can’t wait for it to become ubiquitous on every desktop! The program is called psr.exe; you can also search for it from Control Panel under “Record steps to reproduce a problem”.
WINDOWS 7 DISPLAY PROJECTION
Display Projection
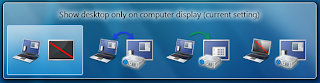
Had enough of messing around with weird and wonderful OEM display driver utilities to get your notebook display onto an external projector? In that case, you’ll be pleased to know that projection is really quick and simple with Windows 7. Just hit Win+P, and you’ll be rewarded by the following pop-up window:
Use the arrow keys (or keep hitting Win+P) to switch to “clone”, “extend” or “external only” display settings. You can also access the application as displayswitch.exe.
If you want broader control over presentation settings, you can also press Win+X to open the Windows Mobility Center, which allows you to turn on a presentation “mode” that switches IM clients to do not disturb, disables screensavers, sets a neutral wallpaper etc. (Note that this feature is also available in Windows Vista.)

Had enough of messing around with weird and wonderful OEM display driver utilities to get your notebook display onto an external projector? In that case, you’ll be pleased to know that projection is really quick and simple with Windows 7. Just hit Win+P, and you’ll be rewarded by the following pop-up window:
Use the arrow keys (or keep hitting Win+P) to switch to “clone”, “extend” or “external only” display settings. You can also access the application as displayswitch.exe.
If you want broader control over presentation settings, you can also press Win+X to open the Windows Mobility Center, which allows you to turn on a presentation “mode” that switches IM clients to do not disturb, disables screensavers, sets a neutral wallpaper etc. (Note that this feature is also available in Windows Vista.)
Subscribe to:
Comments (Atom)



